Content sniffing vulnerabilities pose significant risks to web applications, including WordPress sites. These vulnerabilities occur when a browser attempts to determine the content type of resources based on the content rather than relying on HTTP headers. While this technique can sometimes be beneficial, it can lead to serious security issues if an attacker can manipulate the content being served.
To put it simply, content sniffing allows browsers to “sniff” the type of a file being uploaded or linked to—like images, scripts, or styles—without respecting the content type specified in the response headers. This can potentially lead to scenarios where malicious users can execute scripts or serve harmful content in a way that seems legitimate to unsuspecting users.
Here are some key points to understand:
- Risk of XSS (Cross-Site Scripting): By tricking the browser into interpreting a file as executable code, attackers can inject malicious scripts.
- Insecure File Serving: Files served without strict content-type headers can result in unexpected browser behaviors.
- Increased Attack Surface: If a site allows file uploads without proper validation, content sniffing can turn a benign file into a weapon.
By being aware of these vulnerabilities, developers and site owners can take proactive measures to ensure their WordPress sites are protected.
What is Content Sniffing?

Content sniffing is a technique used by web browsers to assess and identify the type of content being delivered by a server. Often, web servers specify the content type in HTTP headers, indicating whether a file is an image, text document, or script. However, when browsers encounter files, they sometimes try to “sniff” the actual content to figure out its type, disregarding the server’s instructions.
This adaptive behavior can lead to some complex issues. While it is meant to enhance user experience, it also opens the door to security risks. Here’s how it works:
- Basic Principle: If the server incorrectly labels a file type, the browser may interpret it in a way that poses risks to users.
- Detection Logic: Browsers analyze the content and may execute it based on what they “think” it is.
- Safety Concerns: Malicious actors can exploit this by uploading harmful scripts disguised as harmless files.
In short, while content sniffing can enhance usability, it creates vulnerabilities that developers should mitigate, especially in WordPress applications, to ensure that users are safe while browsing. Awareness and prevention strategies are key!
Common Threats Associated with Content Sniffing
Content sniffing vulnerabilities are like the sneaky little gremlins of the web world. They can easily exploit weaknesses in your WordPress site, causing a host of issues that can damage both user trust and site integrity. Let’s break down some common threats that stem from content sniffing:
- Cross-Site Scripting (XSS): This is one of the most dangerous threats associated with content sniffing. Attackers can inject malicious scripts that run on users’ browsers, potentially allowing them to steal cookies, session IDs, or sensitive data.
- Data Exfiltration: By tricking the browser into interpreting files incorrectly, hackers can access user data, including passwords or credit card info, leading to severe breaches of trust.
- Content Spoofing: Cybercriminals can use content sniffing to change how legitimate files are interpreted. This could lead users to believe they are on a secure site, when in fact, they are being directed to a malicious one.
- Denial of Service (DoS): Attackers can exploit content sniffing to overload your website through malicious payloads, potentially bringing your WordPress site down temporarily.
- Phishing Attacks: By misleading users into believing they are interacting with a trustworthy site, attackers can gather sensitive information, further perpetuating the cycle of cybercrime.
Understanding these common threats is the first step in preparing your WordPress site to fend them off. With the right defenses in place, you can ensure you’re not just another target on the web.
How Content Sniffing Affects WordPress Sites
Content sniffing can have a range of effects on WordPress sites, depending on how your site is configured and the level of security measures you have in place. Here’s how these vulnerabilities can manifest:
- Security Breaches: If your WordPress site allows for unvalidated user uploads, content sniffing can lead to a complete breach, giving hackers backdoor access.
- Reputation Damage: If users are frequently encountering phishing schemes or malware while trying to access your site, the trust factor diminishes quickly. This leads to long-lasting damage to your site’s reputation.
- Loss of User Data: Sensitive information might be at risk if attackers successfully exploit your site through content sniffing, leading to potential identity theft for your users.
- Increased Maintenance Costs: Dealing with content sniffing vulnerabilities might require constant updates and security patches, making it more cumbersome and costly to manage your WordPress site efficiently.
- Legal Repercussions: If user data is compromised, you might face legal challenges due to non-compliance with regulations like GDPR or CCPA, which are designed to protect user data.
In short, content sniffing isn’t just a technical issue; it’s a significant threat that affects the overall health and security of your WordPress site. Understanding the impact is crucial for implementing effective countermeasures.
Best Practices to Prevent Content Sniffing in WordPress
Prevention is always better than cure, especially when it comes to securing your WordPress website against content sniffing vulnerabilities. Here are some best practices that can help you keep your site secure and protect your users:
- Use the Right Content-Type Headers: Always ensure that your web server is delivering the correct Content-Type headers for your files, like text/html for HTML files and application/pdf for PDF files. This helps browsers understand how to handle the content without guessing.
- Implement Content Security Policy (CSP): A strong CSP can significantly mitigate the risk of content sniffing. By specifying which resources are allowed to be loaded, you restrict what browsers can do with your content.
- Keep Plugins and Themes Updated: Outdated or poorly coded plugins/themes can introduce vulnerabilities. Regularly check for updates and patch any security holes that might expose your site to content sniffing risks.
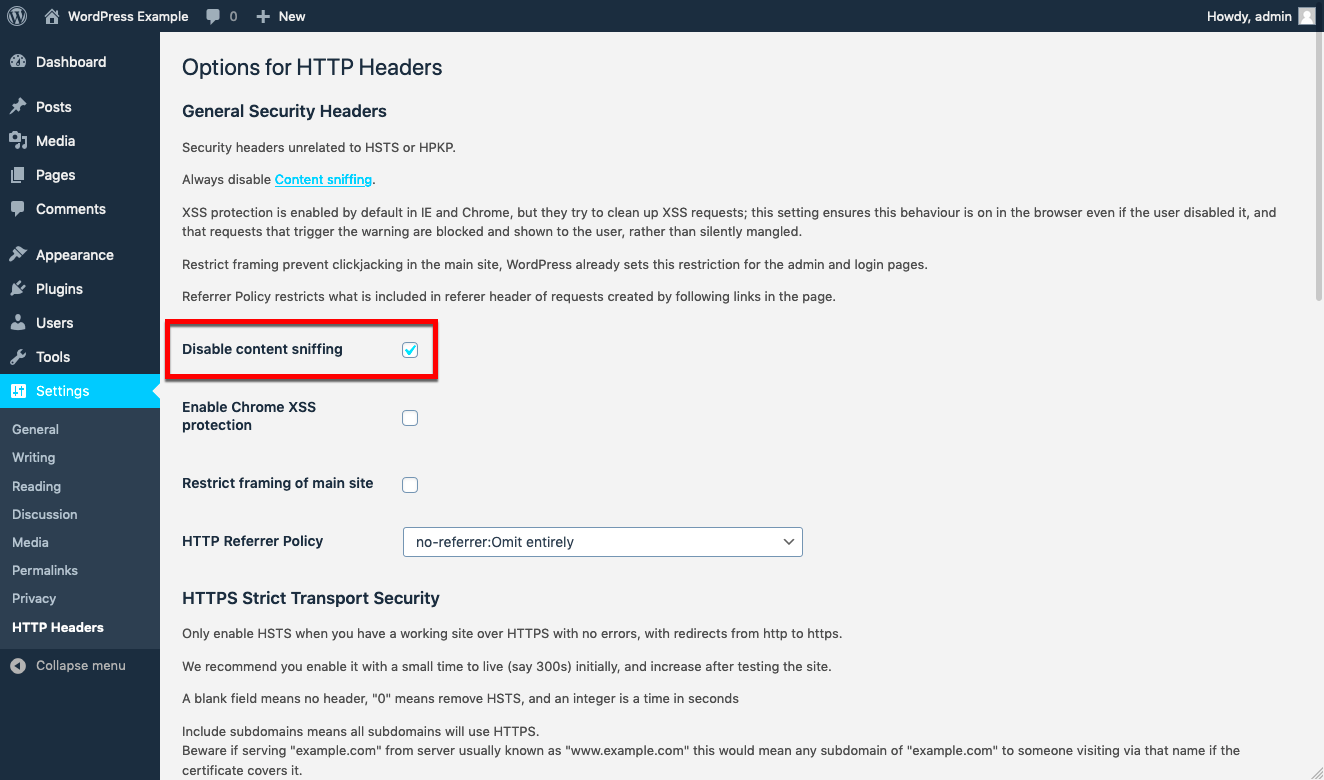
- Disable Content Sniffing in Browsers: Use the X-Content-Type-Options header with the value “nosniff” to instruct browsers not to perform content sniffing. This simple step can prevent potential attacks.
- Review User-Generated Content: Be cautious with user submissions. Always sanitize and escape user input to eliminate any chance of harmful content being executed on your site.
By implementing these best practices, you can create a formidable defense against content sniffing vulnerabilities on your WordPress site. Remember, being proactive is key!
Configuring HTTP Headers for Content Security
Configuring HTTP headers is a crucial part of enhancing your site’s security. Let’s dive into how you can effectively set these headers to prevent content sniffing vulnerabilities:
| Header | Value | Description |
|---|---|---|
| X-Content-Type-Options | nosniff | This header prevents browsers from interpreting files as a different MIME type than what is specified, reducing the risk of content sniffing. |
| Content-Security-Policy | default-src ‘self’; | A CSP directive that specifies only allowing resources from the same origin. You can expand this directive based on your needs. |
| Strict-Transport-Security | max-age=31536000; includeSubDomains; | Enforces the use of HTTPS and ensures all communications are secured for browsers that support this header. |
To add these headers, you can modify the .htaccess file if you’re using Apache, or adjust settings in your NGINX configuration file. Here’s how you might do it:
# Apache .htaccess exampleHeader set X-Content-Type-Options "nosniff"Header set Content-Security-Policy "default-src 'self';"Header set Strict-Transport-Security "max-age=31536000; includeSubDomains;"
By carefully configuring these headers, you’re actively blocking potential content sniffing attempts, making your WordPress site a safe space for your users. Security is all about layers, so don’t hesitate to combine efforts!
Utilizing Security Plugins for Enhanced Protection
When it comes to guarding your WordPress site against content sniffing vulnerabilities, using security plugins can be a game changer. These plugins are like the bouncers at the entrance of a nightclub — they help keep unwanted guests and potential threats at bay. But what should you look for in a security plugin?
- Malware Scanning: A good security plugin should routinely scan your website for malware. This ensures that any malicious code that could exploit content sniffing bugs is detected before it causes harm.
- Firewall Protection: Many plugins come equipped with a web application firewall (WAF). This crucial barrier helps filter out harmful traffic before it reaches your website.
- Login Security: Look for features like two-factor authentication (2FA) and limit login attempts. These functionalities help keep unauthorized users from trying to access your site and sniffing out content.
- Security Audits: Regular security audits provided by plugins can help identify which areas of your site are vulnerable and recommend steps to fortify them.
- Automatic Updates: Some plugins automatically update themselves, which means you won’t have to worry about using outdated security protocols that could leave your site exposed.
In conclusion, installing a reliable security plugin is a proactive measure that significantly reduces the likelihood of content sniffing vulnerabilities. Not only will it protect you from current threats, but it will also keep you prepared for those that may arise in the future.
Regularly Updating Your WordPress Core, Themes, and Plugins
Keeping your WordPress core, themes, and plugins up to date is crucial for maintaining the security of your website. Think of updates as your website’s health check-ups. Ignoring them is like skipping out on routine visits to the doctor — it increases vulnerability and potential risks.
Here’s why regular updates matter:
- Security Patches: Developers regularly release updates to fix security loopholes. Skipping these updates means leaving your site open to content sniffing vulnerabilities that could easily be patched.
- Improved Performance: Updates not only include security fixes but also optimizations that enhance the performance of your site. A faster site can lead to better user experience and higher retention rates.
- New Features: Along with security enhancements, updates often come with new features that can improve the functionality of your website. This could include better content management tools or faster loading times.
- Compatibility: Regularly updating your themes and plugins ensures they work seamlessly with the latest version of WordPress. Compatibility issues can lead to vulnerabilities and potential content sniffing attacks.
How can you stay on top of updates?
| Action | Description |
|---|---|
| Set Up Notifications | Enable notifications for when updates are released, so you’re always informed. |
| Schedule Regular Checks | Make it a habit to check for updates weekly or even bi-weekly. |
| Create Backups | Always back up your site before applying updates. This way, you can revert if something goes wrong. |
In summary, regularly updating your WordPress core, themes, and plugins is vital for safeguarding your website from content sniffing vulnerabilities and ensuring it performs at its best.
9. Conducting Security Audits and Vulnerability Scans
When it comes to safeguarding your WordPress site from content sniffing vulnerabilities, regular security audits and vulnerability scans are crucial. Think of these processes as routine check-ups for your website, allowing you to identify and rectify potential security issues before they can be exploited.
First things first, a security audit involves a thorough examination of your website’s security posture. It helps identify vulnerabilities that could be exploited by attackers, including weak passwords, outdated plugins, and insecure server configurations. Here’s a step-by-step guide to conducting a basic security audit:
- Review User Access: Check who has access to your site and ensure only necessary users have elevated permissions.
- Update Everything: Ensure your WordPress core, themes, and plugins are up to date to protect against known vulnerabilities.
- Check for Insecure Content: Look for any non-HTTPS content, as this can expose your site to man-in-the-middle attacks.
- Review Firewall Settings: Make sure your web application firewall (WAF) is properly configured to block malicious requests.
- Run Vulnerability Scans: Utilize tools like WPScan or Sucuri to run scans and uncover potential vulnerabilities.
In addition to periodic audits, conducting regular vulnerability scans is equally essential. These scans automatically check for known vulnerabilities and can alert you to issues in real-time. The more proactive you are, the better protected your site will be from content sniffing and other security threats.
10. Conclusion: Securing Your WordPress Site Against Content Sniffing
In wrapping up our guide on preventing content sniffing vulnerabilities in WordPress, it’s clear that security isn’t a one-time effort; it’s an ongoing process. By implementing the strategies we’ve discussed, you can dramatically reduce your risk and secure your website against potential threats.
Start by adopting strict Content Security Policies (CSP), ensuring proper content types are declared, and regularly auditing your site for vulnerabilities. Here’s a quick recap of what you can do:
- Utilize HTTP Headers: Implement headers like
X-Content-Type-Options: nosniffto prevent browsers from content sniffing. - Regularly Update Your Site: Keeping your WordPress installation, themes, and plugins up to date helps patch known vulnerabilities.
- Conduct Security Audits: Regularly check your site’s security configuration and access permissions to stay one step ahead of potential attackers.
- Employ Reliable Security Plugins: Consider using trusted security plugins to bolster your defenses.
Remember, every small step you take towards enhancing your website’s security helps create a safer online environment for your visitors. Secure your WordPress site today, and you won’t just defend against content sniffing; you’ll foster trust and confidence among your audience!