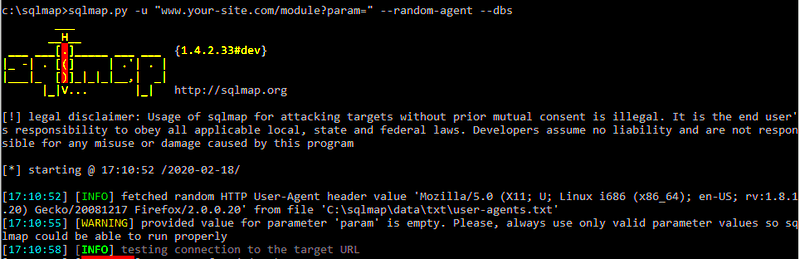
SQLmap is a powerful and popular open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities in web applications. Designed with both novice and expert users in mind, SQLmap offers a user-friendly interface and a plethora of features that make it an essential part of any security professional’s toolkit.
With its ability to support a wide variety of databases, including MySQL, PostgreSQL, and Microsoft SQL Server, SQLmap can be effectively utilized to identify security weaknesses in diverse web applications. Whether you’re a web developer looking to ensure your site is secure or a security auditor performing a comprehensive assessment, SQLmap has got you covered!
Why Use SQLmap for WordPress Security Testing?
When it comes to WordPress security, leveraging the right tools can make all the difference. SQLmap stands out for several compelling reasons:
- Automated Testing: SQLmap automates the detection process of SQL injections, saving you time and effort, especially when dealing with multiple endpoints.
- Efficient Exploitation: Besides identifying vulnerabilities, SQLmap can also help exploit them to demonstrate the severity of the security flaws you’ve discovered.
- Customizable Options: With a range of options to tailor your testing, you can configure SQLmap to suit your specific testing scenarios, including specifying the database type or injection techniques.
- Reporting Features: SQLmap provides detailed reports that highlight discovered vulnerabilities, making it easier to convey your findings to clients or stakeholders.
- Wide Compatibility: Since many web applications use SQL databases, SQLmap’s functionality is beneficial for a broad range of WordPress plugins and themes.
Using SQLmap for WordPress security testing not only enhances your security assessments but also instills greater confidence in the safety of your web applications. Remember, a proactive approach to security is always better than a reactive one!
Installing SQLmap

Installing SQLmap is a pretty straightforward process, and whether you’re using Windows, macOS, or Linux, you’re covered. SQLmap is a powerful tool that helps security professionals and developers identify SQL injection vulnerabilities in web applications, especially WordPress sites. Let’s dive into how you can get this handy tool up and running.
First things first, you’ll need to have Python installed since SQLmap is a Python-based tool. If you don’t have it yet, you can easily download the latest version from the official Python website.
Once Python is installed, here’s how to install SQLmap:
-
Download SQLmap: Head over to the official GitHub repository. You can either clone the repository using Git or download the zip file directly.
-
Clone using Git: Open your terminal and run:
git clone https://github.com/sqlmapproject/sqlmap.git
-
Navigate to the SQLmap Directory: Once you’ve downloaded or cloned SQLmap, navigate into the SQLmap directory:
cd sqlmap
-
Run SQLmap: To execute SQLmap, use the following command in the terminal:
python sqlmap.py
This will present you with various options that you can use for testing SQL injection vulnerabilities.
And that’s it! You now have SQLmap installed and ready to assist you in testing your WordPress site’s security against SQL injection attacks.
Understanding SQL Injection
SQL injection is a significant security vulnerability that can have devastating impacts on a website, including your beloved WordPress site. To put it simply, SQL injection occurs when an attacker can manipulate a website’s database by injecting malicious SQL queries through input fields. This kind of attack can let a hacker perform unauthorized actions, such as accessing sensitive data, modifying records, or even wiping your database clean.
Here’s a bit more detail on how SQL injection works:
-
User Input: When users input data into forms (like login forms, search boxes, etc.), that data is typically sent to the database using SQL queries.
-
Vulnerable Query: If the application doesn’t properly validate or sanitize this input, unsanitized input could lead to an attacker crafting a malicious SQL query.
-
Exploiting the Database: The attacked input can alter the SQL statement sent to the database. For example, instead of just trying to log in with a username and password, the attacker might input something like:
' OR '1'='1
This could allow them to bypass authentication entirely!
SQL injections can result in:
- Unauthorized viewing of data
- Deletion or alteration of records
- Data exposure, including sensitive information
Awareness about SQL injection is crucial, especially when managing a website. Knowing that it’s a potential risk helps you take the right precautions. By regularly testing your website with tools like SQLmap, you can identify vulnerabilities and take steps to secure your WordPress site against such threats.
5. Setting Up Your WordPress Testing Environment
Alright, so you’ve decided to dive into the world of WordPress security testing. Great choice! But before we get into the nitty-gritty, you’ll need a reliable testing environment. Here’s how you can set it up efficiently.
First things first, it’s important to have a dedicated testing environment separated from your live site. This way, you can experiment without the fear of breaking anything on your actual website. A popular approach is to use a local server for this purpose. You can install software like XAMPP or MAMP, which allows you to run PHP and MySQL on your own computer.
Once you have your local server up and running, follow these steps:
- Install WordPress: Download the latest version of WordPress from the official website and extract it into your local server directory.
- Set Up MySQL Database: Use the phpMyAdmin interface to create a new MySQL database for your WordPress site.
- Configure wp-config.php: Update the wp-config.php file with your database name, user, and password.
- Install Plugins: To mimic a more realistic environment, install plugins that you commonly use on your live site. This adds some complexity and provides a more accurate testing ground.
Remember to keep your environment secure yet accessible. You might want to use password protection for your local environment, so only you can access it. Once that’s done, you’re all set to start testing! With a solid foundation in place, you’ll ensure that your security assessments are as effective and informative as possible.
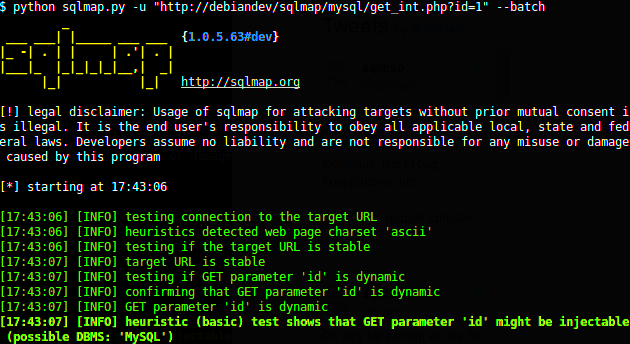
6. Basic SQLmap Commands for WordPress
Now that you have your testing environment up and running, let’s talk about SQLmap. It’s a powerful tool that automates the process of detecting and exploiting SQL injection vulnerabilities. Once you’re ready to begin, knowing the basic commands is crucial for efficient usage.
Here’s a snapshot of some fundamental SQLmap commands that you will frequently use while testing your WordPress setup:
| Command | Description |
|---|---|
| sqlmap -u “http://yourwordpresssite.com/page.php?id=1” | This command initiates a basic SQL injection test against the specified URL. |
| –dbs | List all databases on the server. Add this to the above command to see the databases. |
| –tables -D database_name | Displays all tables in a specified database. |
| –columns -T table_name -D database_name | Retrieves columns for a particular table from a specified database. |
| –dump -T table_name -D database_name | This command extracts data from the specified table in the database. |
These commands serve as essential building blocks when you’re starting with SQLmap. As you progress, you might want to explore additional options and parameters, but mastering these basics will get you well on your way to effectively using SQLmap for WordPress security testing. Happy testing!
Advanced SQLmap Techniques
Once you’ve got a grasp on the basics of using SQLmap, it’s time to dive deeper into some advanced techniques that can really enhance your SQL injection testing. By utilizing these advanced features, you can make your security assessments more thorough and effective. Here are some techniques you might find valuable:
- Using Tamper Scripts: SQLmap comes with a collection of tamper scripts that can help evade web application firewalls (WAFs). These scripts modify your requests to be less likely to trigger security systems. To apply a tamper script, use the
--tamperoption followed by the script name. - Custom Payloads: Sometimes, the default injection payloads just don’t cut it. You can create your own payloads or tweak existing ones by using the
--sql-shelloption to interactively craft your queries. This can be handy for testing specific database configurations. - Data Extraction: Beyond just detecting vulnerabilities, SQLmap allows you to extract valuable data from the database. Use commands such as
--dumpto retrieve entire tables or--tablesto view specific databases. - Using Proxy: If you want to monitor the requests SQLmap sends to the server, use the
--proxyoption. This is great for debugging or understanding how SQLmap interacts with the target application. - Using Multiple Threads: Speed up your testing by using the
--threadsoption. This allows SQLmap to run multiple requests simultaneously, significantly reducing the time it takes to complete a testing session.
Armed with these advanced techniques, you can take your SQL injection testing to the next level. Remember, the goal is to understand not just the surface of vulnerabilities, but their potential impact and how they can be remedied.
Analyzing SQLmap Output
Once you run SQLmap against a WordPress site, the next step is to understand the output it generates. Analyzing this output is crucial for determining the security posture of the application. Here, we’ll break down some key aspects of the SQLmap output that you should pay attention to:
| Output Component | Description |
|---|---|
| Vulnerability Report | SQLmap will indicate whether or not the target is vulnerable, and it will outline the types of SQL injection it detected (e.g., boolean-based, error-based). |
| Database Management System | The output will typically reveal what kind of database the application is using (MySQL, PostgreSQL, etc.), which is important for tailoring your mitigation strategies. |
| Extracted Data | If you’ve opted to extract data, SQLmap will list databases, tables, and even specific rows depending on your commands. Review this data carefully as it may reveal sensitive information. |
| Time Taken | The output often includes how long SQLmap took to run the tests. This is useful for understanding the load your tests put on the server. |
While assessing the output, remember to look for any red flags such as sensitive data availability or improper configurations. Each piece of information SQLmap provides is a vital clue that you can use to enhance your WordPress site’s security. It’s not just about finding vulnerabilities—it’s also about understanding their implications.
9. Best Practices for Securing WordPress Against SQL Injection
When it comes to securing your WordPress site from SQL injection attacks, adopting best practices is the best line of defense. These practices not only help fortify your WordPress installation but also enhance its overall security. So, let’s dive into some effective strategies!
- Keep WordPress Up to Date: Always ensure you’re running the latest version of WordPress along with its themes and plugins. Developers frequently release updates that patch security vulnerabilities, so staying updated is crucial.
- Use Trusted Themes and Plugins: Only download themes and plugins from reputable sources, such as the official WordPress repository. Avoid using nulled themes or plugins, as they often come with hidden vulnerabilities.
- Implement User Input Validation: Always validate and sanitize user inputs. Use WordPress functions like
sanitize_text_field()oresc_sql()to clean data before it is processed or stored in the database. - Employ Prepared Statements: If you’re writing custom queries, make sure to use prepared statements. This ensures that user input is treated as data, not executable code, thus minimizing SQL injection risks.
- Limit Database Privileges: Use a dedicated database user with restricted permissions for your WordPress installation. This user should not have access to sensitive operations like altering database structures.
- Implement a Web Application Firewall (WAF): A WAF can help filter out malicious traffic before it even reaches your website, providing an extra layer of security against SQL injections and other attacks.
- Regular Backups: Keep regular backups of your WordPress site. In case of an attack, you can easily restore your site to a previous, secure state.
By incorporating these best practices into your WordPress security routine, you’ll greatly reduce the likelihood of falling victim to an SQL injection attack, ensuring your website remains safe and sound!
10. Conclusion
In today’s digital landscape, securing your WordPress site against SQL injection attacks is not just an option; it’s a necessity. SQLmap is an invaluable tool for identifying vulnerabilities and testing your defenses, but it’s up to you to implement and maintain security best practices. Remember, even the most robust security measures can falter if neglected.
While tools like SQLmap can highlight weaknesses, it’s essential to cultivate a comprehensive security mindset that includes:
- Regular updates and patching of software
- Strict validation and sanitization of user inputs
- Establishing user roles with minimal privileges
- Using trusted plugins and themes only
- Implementing robust backup solutions
By remaining vigilant and proactive, you can significantly reduce the risk of SQL injection attacks on your WordPress site. So, take these insights to heart and start securing your website today!