In recent times, data breaches have become increasingly common, posing risks to personal information and digital assets, including photographs. EyeEm, a popular photography platform, experienced a significant data breach that has raised concerns among its users. Understanding the implications of this breach and knowing how to safeguard your photos is crucial for photographers and enthusiasts alike.
Understanding the EyeEm Data Breach

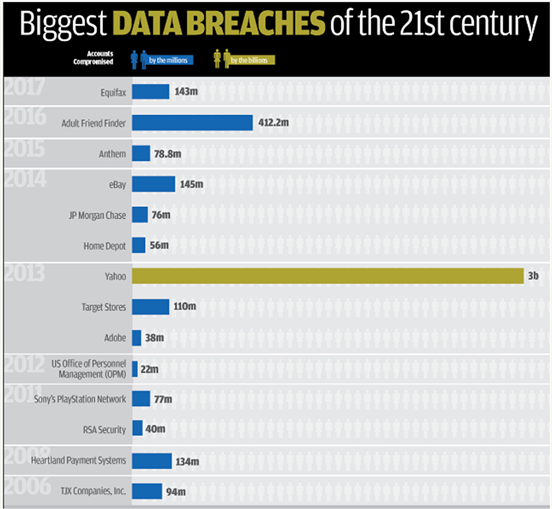
The EyeEm data breach involved unauthorized access to user accounts, which may have exposed personal and sensitive information. This breach has implications for individuals who rely on online platforms to store and share their photos. When a data breach occurs, hackers can leverage stolen information to commit identity theft, unauthorized photo use, or even sell images without permission.
It’s essential to know that the extent of the breach can vary, affecting not just user accounts but also their content and associated data. Users might find their photos compromised, leading to potential misuse or unauthorized publication. This can have significant consequences, especially for professional photographers who rely on their work for livelihood.
Why Your Photos are at Risk
Your photos are at risk due to several factors associated with data breaches. First, many users tend to reuse passwords across multiple platforms, which can facilitate unauthorized access if one account is compromised. Second, inadequate security measures, such as missing two-factor authentication, can make it easier for hackers to infiltrate accounts. Additionally, the nature of online sharing can expose images to a broad audience, making it difficult to control their distribution.
Furthermore, once a photo is shared online, it can be challenging to retrieve or remove it if it falls into the wrong hands. Consequently, understanding these risks and taking preventive measures is vital in protecting your cherished images from potential threats.
Alternative Platforms for Photo Storage
If you’re concerned about the recent data breach at EyeEm, it might be a good time to explore alternative platforms for storing and sharing your photos. There are several reliable options available that prioritize privacy and security, ensuring your precious memories are kept safe. Here are some noteworthy alternatives:
- Google Photos: A popular choice for its automatic backup feature and easy sharing options, Google Photos offers 15 GB of free storage before you need to consider their paid plans.
- Flickr: Great for photographers, Flickr allows you to store up to 1,000 photos for free. It also has a vibrant community and sharing capabilities tailored for photography enthusiasts.
- Dropbox: Known for its simplicity and security, Dropbox provides a seamless experience for storing files, including photos. With 2 GB of free storage, it’s perfect for more organized storage needs.
- Amazon Photos: If you’re an Amazon Prime member, you get unlimited photo storage with Amazon Photos, making it a convenient option. Plus, it offers file sharing and intelligent organization features.
- pCloud: This cloud storage solution is all about security, offering encryption for your files. You can access your photos from anywhere, and they have a free tier with 10 GB of storage.
When switching platforms, always remember to review their privacy policies and consider the security features they offer. Your photos deserve the best protection!
How to Monitor Your Accounts for Suspicious Activity
After a data breach, it’s crucial to stay vigilant and monitor your online accounts for any signs of suspicious activity. Here are some effective strategies to help you safeguard your accounts:
- Check Login Activity: Regularly review the login activity on your accounts. Many platforms, like Google and Facebook, allow you to see where and when your account has been accessed.
- Set Up Alerts: Enable alerts for any unusual activities on your accounts. This can include unauthorized logins or changes to your account settings.
- Change Passwords: After a breach, it’s wise to change your passwords. Use a mix of letters, numbers, and symbols, and consider using a password manager for extra security.
- Monitor Financial Statements: Keep an eye on your bank and credit card statements for any unauthorized transactions. Report anything suspicious immediately.
- Use Identity Theft Protection Services: Consider enrolling in an identity theft protection service that monitors your personal information across the web and alerts you to potential misuse.
By staying proactive and vigilant, you can significantly reduce the risk of falling victim to the consequences of a data breach. Remember, your security is in your hands!
Legal Rights and Recourse After a Data Breach
Experiencing a data breach can be alarming, especially when it involves your personal photos. It’s essential to understand your legal rights and options if your data has been compromised. Here’s a brief overview of what you need to know:
- Notification Obligations: Companies are often required to inform you if a data breach occurs that affects your personal information. Make sure to check if EyeEm has issued any announcements regarding the breach.
- Your Data Rights: Depending on your location, data protection laws like the GDPR in Europe or the CCPA in California grant you certain rights, including:
- The right to access your data
- The right to request deletion of your data
- The right to rectify incorrect data
- The right to data portability
- Taking Action: If your rights have been violated, consider filing a complaint with a data protection authority or even pursuing legal action. Consult with a legal expert specializing in data privacy for guidance.
- Monitor for Misuse: Keep an eye on your accounts and online presence after a breach. If you notice any suspicious activity, report it immediately. You might also want to consider a credit monitoring service.
It’s important to know that you are not powerless in such situations. Understanding your legal rights is a crucial step in protecting yourself after a data breach.
Frequently Asked Questions About Photo Security
In today’s digital age, protecting your photos is more important than ever. Here are some frequently asked questions that can help you understand more about photo security:
- What should I do if I suspect my photos were compromised?
Take immediate action by changing your passwords for accounts where your photos are stored. Review and enhance your privacy settings. Monitor your accounts closely for any unauthorized access. - How can I secure my photos online?
Consider the following tips: - Use strong, unique passwords.
- Enable two-factor authentication on your accounts.
- Be selective with the platforms you choose to share and store your photos on.
- Are cloud storage services safe for my photos?
While many cloud services use encryption and other security measures, they are not infallible. Always research a service’s security features and read user reviews before uploading sensitive content. - What if my photos are leaked online?
If you find your photos shared without your consent, report the content to the hosting platform immediately. You may also need to consider legal recourse depending on the severity of the situation.
Staying informed and taking proactive steps can help you keep your photos safe in a world where data breaches are increasingly common.