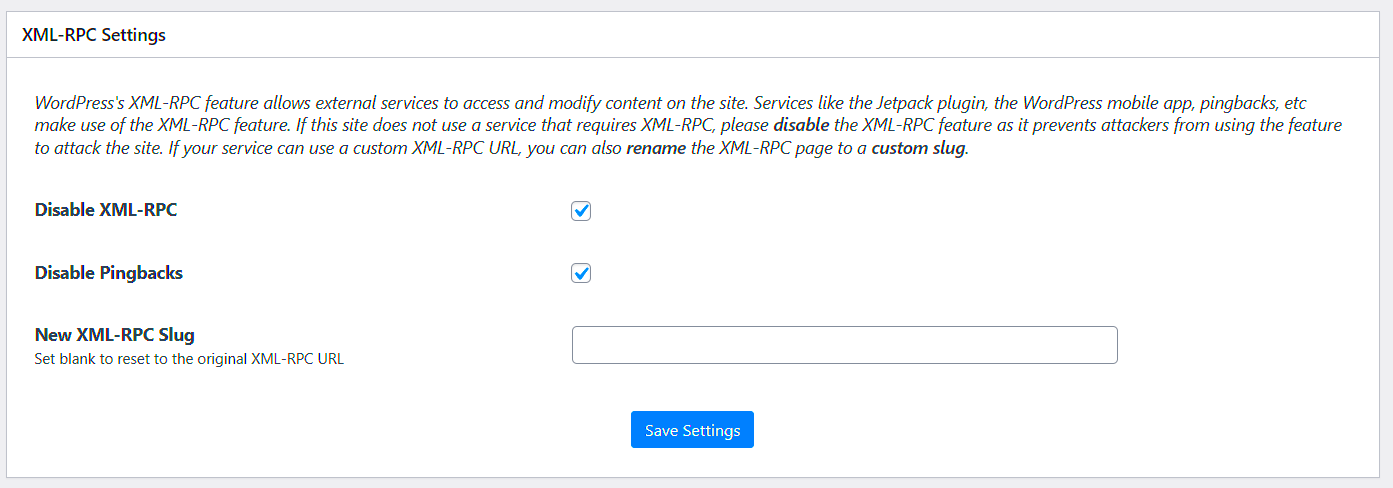
XML-RPC (Extensible Markup Language Remote Procedure Call) is a protocol that allows remote communication with a WordPress website. It enables external services to interact with WordPress, making tasks like posting content, managing comments, and other administrative activities possible from remote locations or applications. However, as convenient as it is, XML-RPC can expose websites to security risks if not properly managed.
Many WordPress users are unaware that XML-RPC is enabled by default on their sites. Unfortunately, this openness can be exploited by attackers. XML-RPC is known to be a target for brute force attacks, where hackers try various username and password combinations to gain unauthorized access. Additionally, vulnerabilities within XML-RPC itself can be exploited for malicious activities. Therefore, it’s important to monitor and control XML-RPC usage to prevent security breaches.
Understanding How XML-RPC Works on WordPress
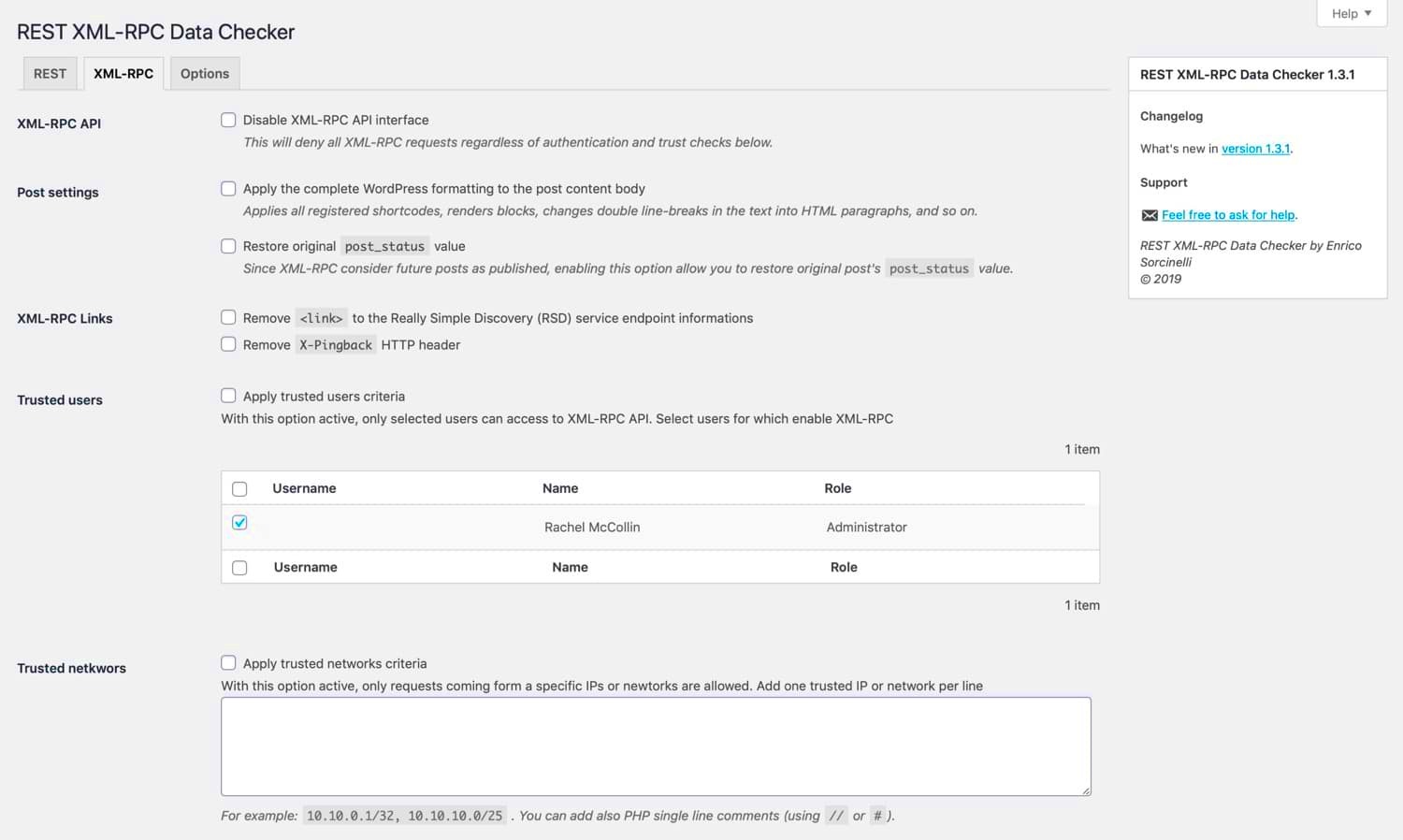
XML-RPC is built on an open standard that allows different systems to communicate with each other using HTTP as a transport and XML as the encoding. WordPress uses XML-RPC to enable remote services and applications to interact with the site. This includes functionalities like posting blog entries, managing comments, and even interacting with mobile apps that communicate with the WordPress site.
Here are some key points to understand about XML-RPC in WordPress:
- Remote Access: XML-RPC allows remote access to your WordPress site from any application or server that supports the protocol.
- Authentication: It uses WordPress’s login credentials for authentication, which can be a target for brute-force attacks.
- Multiple Functions: It enables a range of actions, such as posting content, uploading media, and updating your site’s status remotely.
Despite its usefulness, this functionality often goes unnoticed until it’s too late. Many WordPress users are unaware of how it can potentially compromise their site’s security. Monitoring XML-RPC activity and managing its access are vital for preventing issues.
Reasons to Disable XML-RPC for Better Security
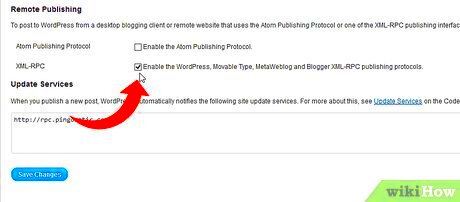
While XML-RPC provides powerful functionality for remote management of a WordPress site, it can also expose vulnerabilities if not carefully monitored. Here are some reasons why disabling XML-RPC might be a good security measure:
- Prevents Brute Force Attacks: One of the most significant security risks with XML-RPC is its use in brute force attacks. Attackers attempt to guess login credentials using automated tools, and XML-RPC’s “multicall” feature makes it easier for them to try multiple username and password combinations in a single request.
- Exposes Sensitive Data: XML-RPC can potentially expose sensitive data, such as your WordPress login credentials, to attackers, especially if your site uses weak passwords or other insecure settings.
- Reduces Attack Surface: Disabling XML-RPC minimizes the number of potential entry points on your website, reducing its overall vulnerability to hackers.
- Prevents DDoS Attacks: XML-RPC can be exploited to perform Distributed Denial of Service (DDoS) attacks, where multiple requests are sent to overwhelm a website’s server. Disabling it can reduce the likelihood of such attacks.
Disabling XML-RPC is a straightforward way to improve your site’s security. It’s especially beneficial for sites that don’t need remote management. By turning off XML-RPC, you eliminate a potential vulnerability without affecting your site’s regular operations.
How to Check If XML-RPC is Enabled on Another WordPress Site
If you’re concerned about the security of another WordPress site, you may want to check whether XML-RPC is enabled on that site. Fortunately, this process is fairly simple and doesn’t require access to the WordPress admin dashboard. Here’s how you can check:
- Using a Browser: To quickly check if XML-RPC is enabled, visit this URL:
http://www.yoursite.com/xmlrpc.php(replace “yoursite.com” with the actual site URL). If you see a response similar to “XML-RPC server accepts POST requests only,” then XML-RPC is enabled. If the server returns a 404 error or a similar message indicating the file is not found, it is likely disabled. - Using Command Line: For more advanced users, you can use a command like
curlto check if XML-RPC is active. Run the following command in the terminal:curl -I http://www.yoursite.com/xmlrpc.php. A 200 OK response indicates XML-RPC is enabled. - Checking for Activity: If XML-RPC is enabled, it might be actively used for posting or updating content remotely. Monitoring log files or server logs can help you detect XML-RPC requests if they’re being made frequently.
Being able to check XML-RPC status on another site can be useful for web developers, security analysts, or anyone responsible for monitoring multiple WordPress sites for potential vulnerabilities.
Methods to Disable XML-RPC on WordPress Sites
Disabling XML-RPC can significantly enhance the security of your WordPress site. If you don’t need remote access or use applications that require XML-RPC, it’s a good idea to turn it off. Here are a few methods to disable XML-RPC on a WordPress site:
- Disabling via Functions File: One common method is adding a snippet of code to your theme’s
functions.phpfile. Add the following code to block XML-RPC:add_filter( 'xmlrpc_enabled', '__return_false' );
This simple line of code will disable XML-RPC requests site-wide.
- Using a Plugin: There are various plugins available to disable XML-RPC functionality. Popular plugins like Disable XML-RPC and Wordfence Security allow you to easily disable XML-RPC without touching any code. Simply install and activate the plugin, and it will take care of the rest.
- Modifying .htaccess File: You can block XML-RPC at the server level by adding the following lines to your site’s
.htaccessfile:RewriteEngine On RewriteCond %{REQUEST_URI} ^/xmlrpc.php$ [NC] RewriteRule ^(.*)$ - [F,L] This will return a 403 Forbidden error when an XML-RPC request is made.
Disabling XML-RPC is an easy yet effective way to protect your site from certain security risks, especially if you don’t use remote applications that require it.
Testing and Verifying XML-RPC Disabling
Once you’ve disabled XML-RPC on your WordPress site, it’s important to verify that the changes have been successfully implemented. Testing ensures that the disabled functionality cannot be accessed by anyone, including attackers. Here are some ways to test and verify that XML-RPC is truly disabled:
- Manual URL Test: The simplest way to test is by navigating to the
xmlrpc.phpfile. Try accessinghttp://www.yoursite.com/xmlrpc.php(replace “yoursite.com” with your actual site). If XML-RPC is disabled, you should see a 404 error or a message saying the file is not found. - Using cURL Command: Run the following command in your terminal:
curl -I http://www.yoursite.com/xmlrpc.php. If XML-RPC is disabled, the response should be a 403 Forbidden or 404 Not Found message. - Third-Party Tools: You can also use online tools like Is It Down Right Now? or other HTTP status checkers to verify that the
xmlrpc.phpfile is returning an error or being blocked. - Server Logs: Check your server logs to ensure no XML-RPC activity is occurring. If requests to
xmlrpc.phpcontinue, then the disabling process may not have worked as expected.
After performing these tests, you can be confident that XML-RPC is no longer active on your site. This ensures enhanced security by removing potential attack vectors.
Common Security Issues Linked to XML-RPC
While XML-RPC can be incredibly useful for remote management of WordPress sites, it can also introduce serious security risks if left unchecked. Hackers can exploit XML-RPC to launch attacks or gain unauthorized access to your website. Below are some common security issues associated with XML-RPC:
- Brute Force Attacks: One of the biggest risks with XML-RPC is its use in brute force attacks. The XML-RPC protocol allows attackers to send multiple login attempts in a single request using the “multicall” feature. This makes it easier for them to guess usernames and passwords in bulk.
- Distributed Denial of Service (DDoS) Attacks: XML-RPC can be exploited to amplify DDoS attacks. Attackers can use XML-RPC to send a large volume of requests, overwhelming a server and causing it to crash or slow down significantly. This is especially dangerous for high-traffic sites.
- Data Leakage: If an attacker gains access to XML-RPC, they could potentially access sensitive data on your site. This includes information like posts, comments, and even user details, depending on the level of access granted to XML-RPC calls.
- Exploitation of Vulnerabilities: Like any protocol, XML-RPC has its own set of vulnerabilities. If not kept up to date, attackers can exploit known weaknesses to gain access or execute malicious code. Vulnerability scanners often target XML-RPC endpoints for this reason.
- Weak Password Exploitation: Since XML-RPC uses WordPress login credentials, it’s vulnerable to attacks on weak passwords. If your WordPress site has weak or common passwords, XML-RPC becomes an easy target for hackers trying to gain access.
By understanding these common issues, WordPress site owners can better safeguard their websites by disabling or securing XML-RPC as needed.
Conclusion
In conclusion, while XML-RPC provides useful functionality for remote management and integrations, it also presents potential security risks. Brute force attacks, DDoS attacks, and data leakage are just some of the threats associated with this protocol. Disabling XML-RPC, or at least limiting its access, is a good practice for WordPress site owners who don’t require remote services. By taking simple steps like using plugins, editing the functions file, or modifying the .htaccess file, you can significantly reduce the chances of your site being targeted by attackers. Regularly testing and verifying that XML-RPC is disabled can ensure your site remains secure. Overall, it’s better to disable XML-RPC if it’s not necessary for your operations, as this can dramatically improve your site’s security posture.
Frequently Asked Questions (FAQ)
Q1: Is XML-RPC required for WordPress to function?
No, XML-RPC is not essential for the basic operation of WordPress. It is primarily used for remote access and interactions with external services, such as mobile apps, blogging platforms, and certain plugins. If you don’t use these features, you can safely disable XML-RPC.
Q2: Can XML-RPC be disabled without affecting my site’s performance?
Yes, disabling XML-RPC should not affect the normal performance of your site. It only affects remote services that rely on it, such as certain plugins or mobile apps. If you’re not using those features, disabling XML-RPC can improve your site’s security without any negative impact on its performance.
Q3: How can I tell if XML-RPC is being used on my site?
You can check whether XML-RPC is enabled by visiting http://yoursite.com/xmlrpc.php. If the page returns a message like “XML-RPC server accepts POST requests only,” it’s enabled. Alternatively, you can check your server logs for XML-RPC-related activity.
Q4: Does disabling XML-RPC affect my SEO?
Disabling XML-RPC will not directly impact your site’s SEO. Since XML-RPC is used for remote interactions rather than search engine crawling, turning it off will not harm your site’s visibility or ranking on search engines.
Q5: How do I re-enable XML-RPC if I need it later?
If you decide you need XML-RPC again, simply reverse the changes you made to disable it. If you disabled it using a plugin, you can reactivate the plugin. If you added code to the functions.php file or modified the .htaccess file, remove the changes to restore XML-RPC functionality.